CyberCamp Instructor Profiles
CyberCamp instructors are the rock stars of the cyber security field, with a deep set of skills, communication skills, and expertise to get the job done. All our instructors are trainer-practioners, where they must work in sectors where they apply the theory we teach you.
They have earned their stripes
Julio Del Cid
Information Security(InfoSec), Industrial Control Systems (ICS), Operational Technology (OT) and Internet of Things (IoT) security
Julio Del Cid is a Senior Cybersecurity Consultant and corporate trainer with expertise in Information Security (InfoSec) and Operational Technology/Internet of Things (OT/IoT) cybersecurity, particularly within Critical Infrastructure (CI) sectors like academia, water, finance, and energy.
He has trained critical infrastructure sectors such as finance, water & sewerage, energy and government essential services departments such as the Victorian Police, ESTA 000, health departments, hospitals and more.
Del Cid has authored multiple Masters-level subject such as HS7020 Cyber Criminology, networks and data communication, information security management, cyber forensics and industry facing micro-credential courses.

Some of my work
The work you see below is some work that involves training critical infrastructure clients. Majority of the photos are from live fire exercises delivered as an Advanced Persistent Threat (APT). Items you will see below are Programmable Logic Controllers (PLCs), Human Machine Interface (HMI) engineering work stations and ransomed machines.


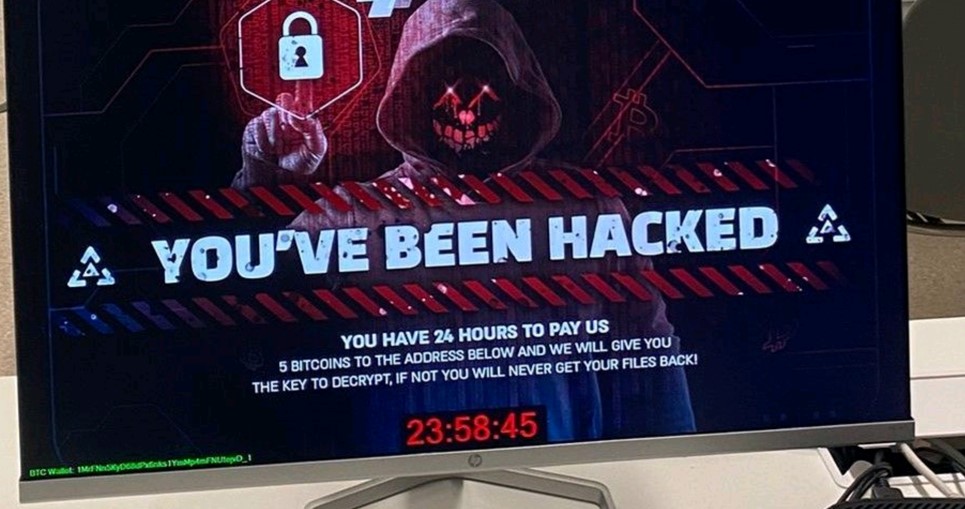
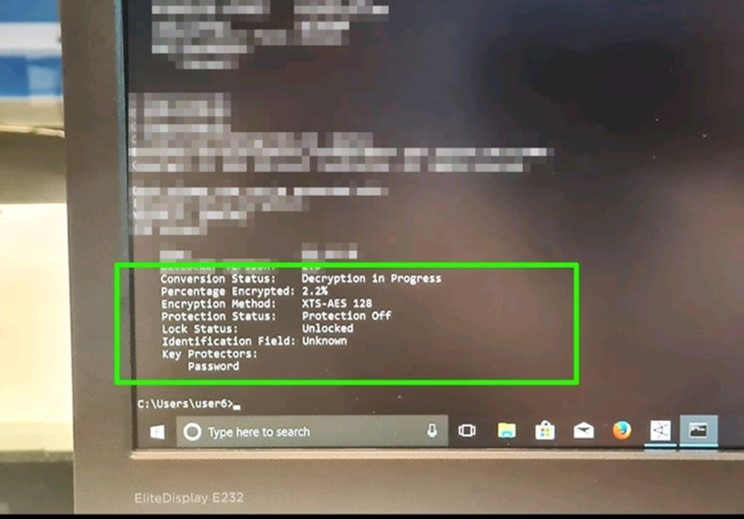
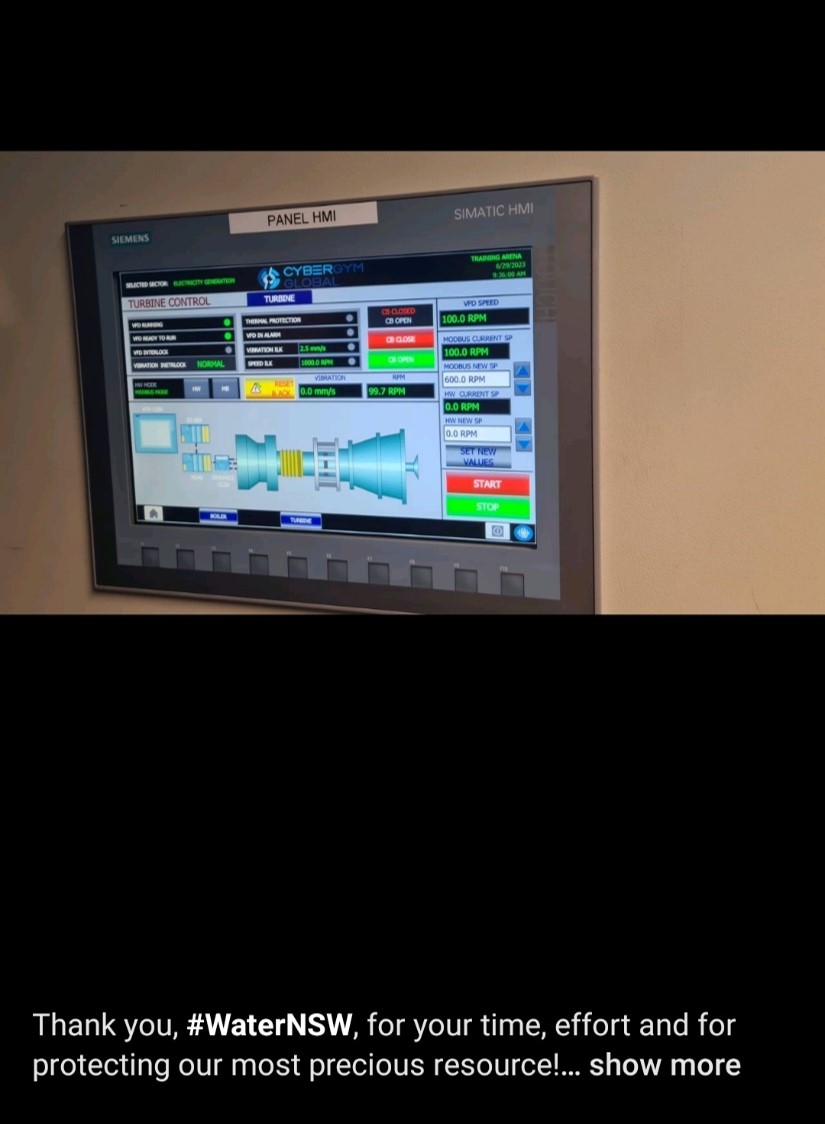

From top left: PLC cabinet which powers turbines and industrial processes seen top right seen in Industrial Control Systems (ICS).
Information security breaches such as initial breaches, ransomware are common place in ICS which can cripple industrial processes as they are co-dependent.
Middle left, BitLocker can work against an operating system and be turned into ransomware, however the WaterNSW team were able to reverse the script.
Bottom left, HMI screen which can show different results to what is actually happening. Integrity attacks should be monitored for authenticity.
Get In Touch

We are located in Melbourne Australia. Please use the contact form so we can get the right staff to contact you. We will the respond via email or setup an initial online meeting, or a face-to-face meeting.
