DECODE introduction and its application
The DECODE (Del-Cid, Education on Cyberpsychology, OSINT, DFIR and Evaluations) framework is a tool that assists humans and machines investigate suspicious and deceptive tactics, technqiues and procedures by humans and machines such as Artificial Intelligence, deep fakes and traditional off-line social engineering deceptive tactis. The framework leverages research created by Julio Del Cid, the author a computer scientist, ex law enforcement (digital forensics and incident response) and cyber security consultant.
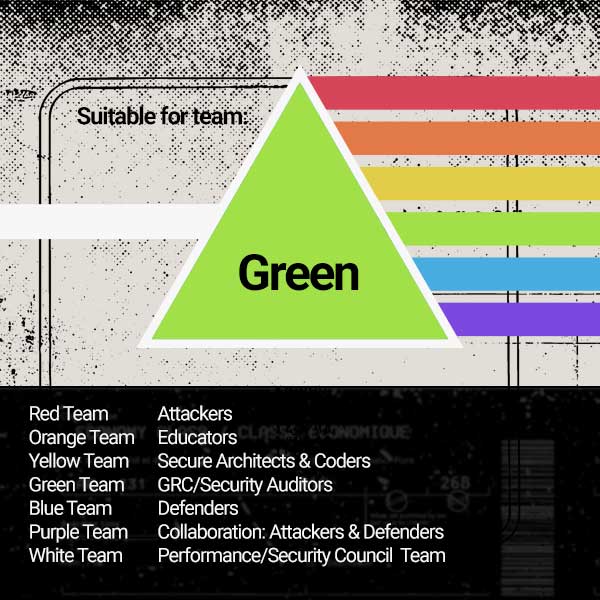
Originally aimed at law enforcement officers, security researchers, and legal professionals dealing with cybercrime this has expanded to the entire cyber security teams (red, blue, purple, orange, white, green, yellow teams). This course is an introduction to the framework, the application and how everyday people can use this reference guide as a way to aid their critical thinking skills.
$199.95
This course only
The DECODE framework is a tool that is becoming an essential tool in a persons arsenal, as the rise of unfiltered content runs rampant on social and website sites. deep fakes using the use of AI and inter-connected physical pbject such as cars, building, homes and critical infrastructure. The DECODE framework assists humans and machines deal with deceptive and counter intelligence TTPs (tactics, technqiues and procedures) created by humans and machines such as Generative Artificial Intelligence (GenAI). The framework leverages research created by Julio Del Cid, the author a computer scientist, ex law enforcement (digital forensics and incident response) and cyber security consultant.
Originally aimed at personnel who interface with computing as an essential part of their role, the general population such as this course can be introduced to what is happening in an unseen world of how humans are leveraging machines as a means to aid their criminal and destructive goals.
What You Will Learn
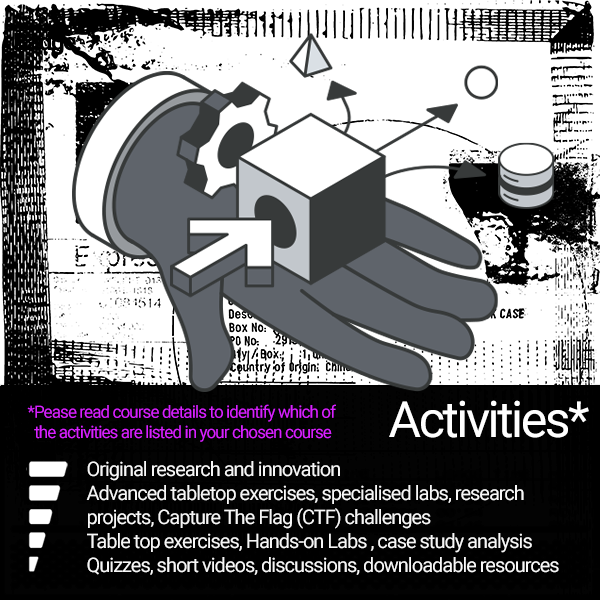
Topics included in this course:
- Comprehensive knowledge of the DECODE framework
- Understanding of the interconnectedness of human factors, technology, and criminal behavior in the digital age
- Ability to apply the framework to real-life situations and case studies
- Develop critical thinking and analytical skills in the context of cyber deception and counterintelligence
Syllabus
Topics included in this introductory course listed below.
Module 1: Introduction to the DECODE Framework
– Overview and key concepts
– The role of human factors in cyber deception
– The interplay of technology and criminal behavior
– Real-life applications and case studies
Module 2: Humans – The Strongest and Weakest Link
– Psychological manipulation and social engineering
– Cognitive biases and critical thinking
– Human factors in cybersecurity incidents
– Counterintelligence and anti-forensic techniques
Module 3: Cyberpsychology
– Online behavior and its offline implications
– Motivations and vulnerabilities of individuals online
– Exploitation of psychological factors for deception
– Strategies for online safety and resilience
Module 4: Cybercriminology
– Application of criminological theories to cybercrime
– Techniques used by cybercriminals for deception and attack
– Investigative methods and frameworks for cybercrime
– Legal and ethical considerations in cybercrime investigations
Module 5: Law Enforcement
– Challenges and opportunities for law enforcement in the digital age
– Legal frameworks and regulations related to cybercrime
– Investigative techniques and technologies for cybercrime
– International cooperation and information sharing
Module 6: Digital Forensics Incident Response (DFIR)
– Methodologies for digital forensics and incident response
– Tools and techniques for collecting and analyzing digital evidence
– Incident response planning and execution
– Legal and ethical considerations in digital forensics
Module 7: Governance
– Key principles of AI governance and ethics
– Risk management frameworks for AI and emerging technologies
– Regulatory and compliance considerations for AI
– Best practices for responsible AI development and deployment
Module 8: Artificial Intelligence
– Basic concepts of artificial intelligence
– Potential threats and risks associated with AI
– How AI can be exploited for malicious purposes
– Ethical considerations and responsible AI development
Module 9: Machine Learning
– Fundamentals of machine learning algorithms
– Vulnerabilities and potential biases in machine learning models
– Best practices for secure and ethical machine learning development
– Techniques for mitigating risks in machine learning applications
Module 10: Deep Learning
– Advanced concepts in deep learning, including neural networks and architectures
– Applications of deep learning in various domains
– Vulnerabilities and security risks in deep learning models
– Techniques for building robust and secure deep learning systems
Module 11: Generative AI
– Capabilities and limitations of generative AI models
– Techniques for detecting and analyzing AI-generated content
– Ethical considerations and potential harms of generative AI
– Strategies for mitigating the risks of malicious use of generative AI
Module 12: Large Language Models (LLMs)
– How LLMs work and their capabilities
– Potential for malicious use of LLMs in disinformation and cyberattacks
– Ethical considerations and responsible use of LLMs
– Strategies for mitigating the risks associated with LLMs
Module 13: Specialised CoBots
– Security vulnerabilities and risks associated with CoBots
– Best practices for securing CoBot systems and preventing unauthorized access
– Incident response and mitigation strategies for CoBot security breaches
– Ethical considerations and responsible use of CoBots
Skills Badge
On completion, you will earn the following badge showcasing your competence. Display your achievements on LinkedIn, personal blogs, and more.

Pathway to an expert
Expertise pathways assist your real-world knowledge, which employers highly value. Each badge helps you be a well-rounded professional by solidifying theory, case studies, law, and technical hands-on understanding.

To learn more about pathways visit https://cybercamp.com.au/pathways/
Before You Start
Pre-requisites. We recommend the following:
- You take the previous level courses
- Knowledge in fundamental computing and networking is usually obtained at the workplace and/or in a study course
- For management and executive level training, a good command of English in written and verbal
Author

Julio Del Cid is a Senior Cybersecurity Consultant and corporate trainer with expertise in Information Security (InfoSec) and Operational Technology/Internet of Things (OT/IoT) cybersecurity, particularly within Critical Infrastructure (CI) sectors like academia, water, finance, and energy. He has trained critical infrastructure sectors such as finance, water & sewerage, energy, and government essential services departments such as the Victorian Police, ESTA 000, health departments, hospitals, and more.
Del Cid has authored multiple Masters-level subjects such as HS7020 Cyber Criminology, networks and data communication, information security management, cyber forensics, and industry-facing micro-credential courses.
More information: https://cybercamp.com.au/julio-del-cid/
Ready to upskill?
Frequently Asked Questions about:
Pathways & Badges
Courses & Pricing
Company & Support
Other & Feedback
Can you explain what pathways are?
Pathways are a logical set of courses that will give you enough knowledge that we deem you to be an expert.

Our definition of an expert:
- Element 1. An expert is a highly qualified individual with deep knowledge and extensive experience in a specific cybersecurity or AI domain. They possess advanced theoretical and practical skills, often holding a Master's degree or Ph.D. and having 10+ years of experience.
- Element 2. Experts at Cyber Camp can serve as expert witnesses in legal proceedings, where they can be cross-examined by the legal jurisdiction and questioned by another expert. They can also participate in peer-reviewing processes, evaluating the work of others in their field.
- Element 3. Experts have added to human knowledge by publishing articles that can serve the community to secure its residents.
What do the badges mean?
Each badge is explained below. 'Industrial Cyber' is used as an example and changes within the domain you specialise in.
![]()
Domain Certified badges:
- Awarded to someone who has completed a course on a topic or domain
- Example fundamental knowledge in industrial cyber security
- Equivalent to a technical college Advanced Diploma level or Associate Degree
![]()
Foundations badges:
- Awarded at the completion of a domain's body-of-knowledge (BoK)
- Foundational knowledge is required for further advanced and expert knowledge as foundational branches into deep-dive learnings
- Foundational BoK is highly recommended knowledge for further courses
- Equivalent to a Bachelor degree subject
![]()
Intermediate badge:
- Awarded to deeper, more complex BoK topics
- Requires hands-on knowledge, such as table top exercises, lab completions, and have an examination element
- Aligned with theoretical knowledge with BoK such as with reputable certifications such as CISSP, CISM, CISA and its equivalent
- Hands-on experience with deep dive technical knowledge
- Equivalent to a post-graduate certificate-level subject
![]()
Advanced badge
- Similar to intermediate but deeper dive complex topics
- Requires hands-on knowledge, such as tabletop exercises, lab completions, and have an examination element
- Aligned with theoretical knowledge with BoK such as with reputable certifications such as SANS Institute, ISACA, ISC2, and its equivalent
- Equivalent to a Masters degree subject
![]()
Expert badge
- Requires completion of prior courses in the Cyber Camp catalogue
- Requires hands-on knowledge, such as tabletop exercises, lab completions or anything that can prove your theorem
- Research and publish a new area of knowledge to benefit human knowledge
- Aligned with theoretical knowledge with BoK, such as with reputable certifications such as SANS Institute and its equivalent
- Equivalent to a PhD degree subject
- Automatically qualifies you to be a corporate trainer
Are these badges worth anything?
Of course, they are, let us highlight the following points:
- The real value is the knowledge you gain throughout the course when you apply the skills in the cybersecurity industry to defend real world information systems/ industrial control systems, a technical interview with indepth questions/challenges and, academic research and everyday knowledge.
- These badges signal to the world you have completed a body of knowledge and to some employers may be that unique skill they need. Skills badges are often published on websites like LinkedIn and are seen by hiring teams as potential candidates, opening opportunities for you and your team
- Some examples:
- Example 1: For many cyber security roles, it is expected you know the CIA triad its counterpart, the DAD (Disclosure, Alteration, Denial) triad and provide examples of case/case law and how to mitigate each threat
- Example 2: For Governance Risk and Compliance (GRC) roles, it's expected you know about the NIST Risk Management Framework, which has special publications and RMF documentation over 900 pages. We shorten this lengthy learning curve to just hours or days for paths.
- Example 3: Industrial control systems security engineers, are expected to know indepth ISA/IEC 62443, industrial networking protocols, ISO 27001, ISO 27002, GDPR, and your local laws as a minimum.
- Example 4: Executives are expected to know the kind of threats, and risk occur on a frequent basis making sure no loss to stakeholders whcih includes knowing how to reduce insurance premiums by applying an aaceptable level of risk that reduces premium costs and secures the organisation from breaches which protect assets not covered by cyber insurance.
Keep in mind that a badge is a far distant second place to the knowledge and hands-on experience you will gain.
How do your courses work?
Each course is a stand alone unit, designed to fufill a knowledge/skills gap that is not readily available.
You can each course as a standalone unit, or in a series such as in a pathway expert, see the "Badges and Pathways" tab for more information.
Access to course materials:
- A single courses grants you access to the course material for one year from the purchase date. Unless you have earned at minimum a 'Foundations' badge.
- Lifetime membership is granted to :
- Code Camp Experts
- Pathway students who earn a Fundamental, Intermediate and Expert badge
Why do some courses have different pricing?
Different courses have different rates, because of the unqiue research and skills required to develop them. Some courses have access to different resources and may cost more than others. At the time of publishing the current * pricing is
- Foundational $199
- Intermediate $299
- Advanced $499
- Expert $899
*For most accurate pricing see plans page.
Why are some so expensive and others are not?
'Cheaper' courses are foundational knowledge and we feel all members of the workforce need to have. Compared to other areas such as advanced and expert courses, where we hired specialists, researchers and required specialist equipment to record the findings for you.
We also compare the quality of intermediate, advanced, and expert courses with that of reputable training institutions such as SANS Institute. Feel free to compare the courses, and reach out to us if we do not fulfill this claim, our team can map out the learnings.
Keep in mind that a typical SANS course will cost in excess of USD $10,000 to obtain, whereas our expert pathway will likely be under USD$1,750. We as does SANS graduates are required to perform hands-on exercises, comprehend a BoK in a technical domain using the latest cutting edge, know how.
Who is CodeCamp?
Cyber Camp is a the result of years of industry experience and corporate training from Julio Del Cid the Chief Author. Cyber camp's foundations are from research and development, inspired by the volume of industry insights from first hand, industry feedback and training ICT seasoned professionals.
"Quality Australian cyber content is hard to come by. Australians need to be trained to protect Australia's infrastructure and its residents from Australian specific content in laws and technology that is familiar with us."
Julio Del Cid (You can see his profile under company page)
Reputable content from the globe is collated such as ISA/IEC 62443, NIST, ISO27000 series, etc and delivered in an Australian context.
What kind of support do you offer?
- We offer ticketed support for indivuals.
- Corporate clients have an account manager which is a direct line to us.
Note: Corporate clients are simply organisations that have 5 seats of more with us. See plans for more information: https://cybercamp.com.au/plans.
Where are you located?
Melbourne, Australia. Contact us to meet in person.
How can we provide feedback?
You can get in touch in two ways:
- Your corporate manager
- Feedback form found on the support page: https://cybercamp.com.au/support/
Browse our entire catalogue of courses
Showing 1–18 of 96 results
-

AI for Administration & Operations in the Education Sector
$299.95 -

AI for Cybersecurity
$499.95 -
AI for Research
$499.95 -
AI for Teaching & Learning
$299.95 -

AI in OT/IoT
$299.95 -

AI Literacy for Non-Technical Professionals
$199.95 -

Australian Energy Sector Cyber Security Framework – AESCSF
$499.95 -

Blue teamer – Defender
$299.95 -

Cyber Security Contractors – Workers interacting with your enterprise
$199.95 -

Cyber Security Critical Infrastrucure in Australia and the globe
$199.95 -

Cyber Security Essentials for Everyday Individuals – Non enterprise
$199.95 -

Cyber Security Essentials for Managers – Non Technical
$199.95 -

Cyber Security Essentials for Operations Staff – Non Technical
$199.95 -

Cyber Security Essentials for Operations Staff – Technical
$199.95 -

Cyber Security Essentials for Technical Managers – Technical
$299.95 -

Cyber Security Essentials for the C-Suite – The Board and Managing Directors
$499.95 -

Cyber Security Essentials for the Chief Artificial Intelligence Officer (CAIO)
$499.95 -

Cyber Security Essentials for the Chief Information Officer (CIO)
$499.95